How often one shares his likings, wishes, and plans with anyone? Guess, not even the closest ones would know about every detail. However, one always reveals every data to the “Modern shadow” that forms a digital copy of the person. Nowadays, information which one wishes to keep up to himself could be acquired by the government, big businesses, and illegal groups.
Privacy is having control over the sharing of the data that an individual or a group has generated through any online or offline activity.
The level of privacy required differs from person to person. One may not be comfortable in revealing his photographs, but the other one would not even mind sharing his location. People safeguard the data to maintain the security, but many don’t consider it as a threat.
Higher the level of privacy, lower the threat to security.
The Connection between Privacy and Security
As we have already mentioned, privacy is having control over the sharing of data. When we provide our information to someone, we consider them as a trustworthy entity, and rely on them that our data would be kept secure. However, if they sell or rent our data to any third-party, our privacy gets compromised if it’s done against our consent or through trickery.
But, if someone gets unauthorized access of the information through data breaching, security gets compromised.
For example, one has made an account on a shopping website.
The data of your related to your search, your session time, the products which interest you more, the region from which you belong, etc. is collected, and then shared with data mining companies which may then work to find patterns through the data of different users. That’s how more hands acquire your data than you know, than you wish, disturbing your privacy.
That helps them to target the correct audience, which increases the sale. However, it won’t be containing any personally identifiable information (PII), and thus, it’s impossible for the third-party to detect that what information belongs to which user.
However, if the data breach occurs because of hacking, poor security, inside job or by accidentally publishing the data, then it questions the security. If cyber-criminals get access to your credit card details, your name, address and contact information that you have added on the shopping website, then it could be harmful, affecting you and your security.
What is Data Breaching?
To understand this in simple terms, let’s have a look over the example of a book. When the data is stored locally, and not connected to any network, it acts like a book placed in one’s room which can’t be accessed by anyone. The person who is interested in the book’s information needs to come to one’s room and find it manually. This is the case without the internet connected.
Now, think of a box where everyone has stored their respective books. Even if they have locked their books, anyone can reach the book through the box. One would just need to break the lock to read anyone’s data. That’s how one’s information over the Internet could be found and breached by anyone. With the internet, reaching to someone’s data has become facile, and that’s why people need to implement trustworthy locks.
Now, the question arises, how hard is it to break the lock? Well, it depends upon the platform that one is using. Different operating systems, browsers, networks, and websites have a different level of security, and it matters a lot that how much they individually care about our privacy, and how much data they store about us.
With time, the data breaching incidents have been increasing. However, initially, it was done with the help of “inside communication” and with “logically deciphering code.” With the changing world and strengthening of security, it isn’t possible every time to break through the system and get information by the above data breaching techniques.
With time, spies were replaced with hackers, letters with e-mail and the new form of information such as credit card details and data generated over social media came into existence.
In the 1980s, around the time when the internet was born, the frequency of disclosure of sensitive private information had shown tremendous growth, and as we entered in the 21st century, the number and impact increased significantly.
Some Notable Examples of Large-scale Data Breaching
Yahoo’s 3 billion accounts compromised without a clue
In the year 2013 and 2014, this data breach incident was conducted which remained unknown till the year 2016 when a third-party reported about it. Initially, it was assumed that 500 million accounts were hacked but later, the investigation reported that all the 3 billion accounts were affected.
It was not known till 2017 that who and how the breach was conducted. According to former Yahoo CEO, Marissa Mayer, the attack was Russian state-sponsored, and there are Russian intelligence officers behind this. However, although the attack is considered complex according to Yahoo, there are possibilities that it might have taken place because of usage of weak and outdated encryption.
Edward Snowden unmasked NSA and the Eyes
Let’s have a look that these eyes consist of which countries:
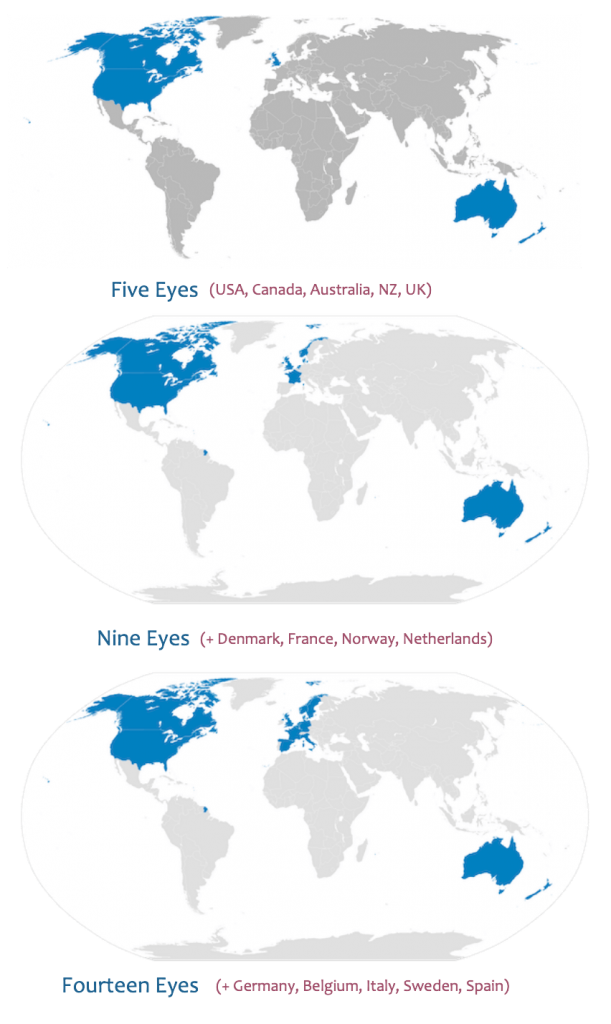
Five Eyes:
- U.S.A
- Canada
- Australia
- New Zealand
- U.K.
Nine Eyes:
- Denmark
- France
- Norway
- Netherlands
Plus, all the Five Eyes Countries.
Fourteen Eyes
- Germany
- Belgium
- Italy
- Sweden
- Spain
Plus, all the Nine Eyes countries.
It was already known for a long time that these countries are helping each other whenever tracking down of data is required. However, before Edward Snowden’s release of NSA’s documents, no one could’ve even guessed that these countries are tracking one another’s every citizen and gathering data about them.
There is the existence of numerous surveillance programs which are performed by these government services to collect the data. In the PRISM surveillance program, the data is collected from the software tycoons that hold the data for millions of users. They also perform upstream collection which is done by directly collecting the data with the help of telecom services, and Internet provider service. One can’t opt out of it, and it’s sure that here his online privacy gets compromised.
Facebook: The Advanced Driller for Mining the Data
Recent data breach which has put Mark Zuckerberg in shame was no less than a shock for every Facebook user. The shock that some strangers know all about the information that one has put on Facebook including the private messages and media
Data analysis works to find important patterns helpful in making the data-driven decision. These decisions are more powerful when the inside information is made available to data analysis companies.
Cambridge Analytica is the best example that we could put here. They had information related to 87 million Facebook users including messages and timeline feed of many users. This helped to identify the interests of the users on a deeper level that not even the people around them would know.
The breach took place with the help of the application, “This is Your Digital Life.” This application was owned by Cambridge Analytica which they used to survey with several hundred thousand Facebook users. Because of Facebook’s design, they were able to get the personal information including the messages and timeline posts through an informed consent process.
Hackers found data on Adult Friend Finder
Hacker instead of an Adult Friend, were more interested in finding the key to the Adult Friend Finder databases. This incident took place in November 2016, after which a data breach notification website, LeakedSource provided the number of exposed accounts.
It was estimated that more than 100 million accounts were breached, but the number goes above 420 million users in the final report. The six databases contain information about the user’s email address, his username, and password which was present in plaintext or it was hashed using SHA1.
The data breach might not have occurred due to the efficiency of the hackers but because of the poor security that Adult Friend Finder provided. Because of this, sensitive information about any account was readily available and sold over the internet.
When Hackers trolled the Indian Government
It was one of biggest government failures when the Aadhar database was hacked. Aadhar is the prominent identity proof for Indian citizens which contains even the information about the biometrics and contact details.
Around one billion accounts were affected after which anyone can get the possession of the information just by paying a few bucks. Not only this, but there are patches which have been used to generate anyone’s Aadhar from anywhere in the world. These patches are actually used to update a software program whenever required. That’s how the hackers alter the functionality of the software and add the information.
Ashley Madison gold-dug by Hackers
Ashley Madison is the online dating site whose data, including PII, was breached in the year 2015. Some users only used the account just once, but after that, they were unable to delete it as Ashley Madison asks to pay if someone wishes to delete the account. However, the breach revealed that they do not delete the data, and the website stores it even after someone pays to delete the account.
The breach hit the emotional site as the data published contained highly personal information which had harmed the reputation of several users. Avid Life Media (parent company) was asked to close the websites, Ashley Madison and Established Men which were unethical according to the hackers.
Two unconfirmed suicides were also reported which were linked to the breached. In total, 30 million email addresses and credit card details of some of the users were also exposed. Many of the Saudi accounts were also exposed, and in Saudi Arabia, adultery can be punished with the death penalty.
One company collected the data from the breach and started a search engine in which anyone can enter the user’s name. If the user’s name matches with the database, the company sends threatening letters asking them to pay the company otherwise their information will be exposed.
This breach has affected the users significantly which would have had long-lasting effects on their lives as the leakage might have caused personal issues.
Mt. Gox: When a Bitcoin was equal to a cent
Bitcoins, everyone thought, would remain free from the fraudulent financial acts happens while one deals with the centralized financial system. However, even cryptocurrencies have their limitations, and in the case of Mt. Gox, a bitcoin exchange company, the limitation was exposed. A hacker, by taking advantage of vulnerabilities of complex security system accessed Gt. Gox auditor’s system and changed the nominal price to one cent.
Nearly 2000 BTC were transferred to the hacker’s account when the price was decreased artificially by himself. Hacker conducting this data breach was never caught, and not a single bitcoin was obtained back. Afterward, to build the confidence of the investors, and for the sake of reputation, the company compensated the stolen bitcoins and placed them in the bitcoin wallet which is not connected to the internet.
Panama Papers: Even wealthies are not safe from data breaches!
Mossack Fonseca & Co. was once the fourth-largest law firm which provided financial services. After the breaching of 11.5 million documents, Panama Papers were published. Panama Papers contains the financial information about many wealthy individuals all over the world, and also have records dating back from the year 1970s.
These records were obtained by the person assumed to have a name, “John Doe.” He hacked through the company’s email server which had poor information security that works with the help of an older version of key tools.
This document has a data size of approximately 2.6 TB and contains information which can put many wealthy individuals behind the bar if legal action is taken against them.
Some Must Know Basics
Data Encryption
Whatever we share over the internet is in the form of plaintext which could be directly obtained by anyone. However, if we use a specified algorithm according to which we change the text, the ciphertext is obtained which one can’t understand without the knowledge of our algorithm. The algorithm is the “Key” according to which one can encrypt and decrypt the data.
The data encryption standard developed by IBM was used as the standard encryption by NSA. However, NSA asked IBM to make a few changes which generated controversy that these changes would allow NSA to eavesdrop if required. After this, implementation of Advanced Encryption Standard was developed which is used by most of the present-day security products and for secure communication.
Two Factor Authentication
Two-factor authentication offers an extra layer of security in addition to a password. It adds a second lock, and the key exists in the information that only you would know. Even Though if someone gets access to the passwords, still, he would need to find a way to get through the second piece of security.
One-time password or SMS verification is widely used by payment gateways and access certain online accounts. After adding the password, the website verifies your identity through the cellular device or e-mail by sending you a code that you need to enter in a specified text box available on the web page.
Physical security keys such as yubikeys were developed which provides two-factor authentication for several websites such as Google, Facebook, and Github. For accessing the account, you need to have physical access to the key which one needs to insert in the USB port and with a tap on the provided button, you get the access of your account. However, before that, you need to log in to your account with the account password.
If one loses the key, and there is no way to recover it, backing up the authentication with applications such as Google Authenticator and authy would be a good idea. These applications generate security codes which change after a specific time. Every time you log in, you need to add this code from the application. So, even if someone has a breach to the company’s database, still he won’t get access to your account because of two-factor authentication.
Strong Passwords
Brute Force is a method of breaking passwords with permutation and combination methodology. It is obvious that shorter the password, lesser the combinations, easier to break. If the password only contains Alphabets, then the number of combinations exists in the form of:
26x [X denotes the password length]
If the use of numbers is included in the password, total combinations exist in the form of:
[26 + 10] x = 36x where 26 denotes the total number of Alphabets and ten stands for the use of 0 to 9.
There are total 32 symbols that are allowed to be added in a password so if one uses them along with the alphabets and number the total combinations that exist are:
[26 + 10 + 32] x = [68] x
Here, we know that the password length is denoted by X, so if we use a password length of two characters the number of combinations would be 68 x 68 = 4624. Even if we increase the password length to five characters the number of combinations increases to 1,453,933,568. So, by increasing length by one character, one gets 68 times more powerful password then the previous one. Thus, the use of symbols, numbers, and alphabet along with a suitable password length will security provide a higher level of security.
HTTPS
HTTPS is a widely used communication protocol that is used over the internet for secure communication. Transport Layer Security is used to create bidirectional encryption between the server and client which helps to protect the data from man-in-the-middle attacks. It provides authenticity to the website that the user access and also ensures a secure connection that could function strongly against data breaching.
Data Theft
Data theft compromises the privacy of the user by stealing the information. The information could be of any type even with a high level of sensitivity. The data could be obtained from any type of source. Generally, the data is stolen from the electronic mediums such as computer and smart phones which could be vulnerable to many intruders which we have mentioned in the later section. Large databases of various websites from the different sector were hacked, and the act of data theft breached. through the privacy of individual
Different Types of Personal Data Breaches & Solutions
Phishing and Keyloggers
Phishing is the methodology of impersonating as a trustworthy identity by which the cyber-criminals acquire user’s sensitive information. This data could be comprised of one’s social security number, credit card information, and passwords. After that, it delivers one’s information to the third-party, without one’s permission, the backend unit which received the data that could be utilized in any way it desires.
Phishing is the methodology of impersonating as a trustworthy identity by which the cyber-criminals acquire user’s sensitive information. This data could be comprised of one’s social security number, credit card information, and passwords. After that, it delivers one’s information to the third-party, without one’s permission, the backend unit which received the data that could be utilized in any way it desires.
One another way by which the cyber-criminals get their hands on our data is through key-loggers. By tracking your keyboard activity, within no time, they can trace your passwords and pins. Keyloggers get installed in the same way like any spyware, but mainly through e-mail attachments.
Even after its harmful use, key-loggers are completely legal as they are used by employers to track their employees’ activities. It is also used in schools and colleges to save students from performing any wrong acts by using educational property. This is also used in parental control software programs such as Windows Keylogger and Actual Keylogger; so that parents could keep an eye on their children’s activity for safeguarding online privacy.
Example
Phishing exists as one of the oldest online con technique. In the year 2009, according to the FBI director of that time, one of the largest international phishing cases was committed. In total, $1.5 million were transferred into fake accounts by duping Hotmail users who revealed their bank details due to this phishing scam.
In the keyloggers, one may not even know that its activities are being tracked as the key-loggers works secretly in the background. Because of Ursnif keylogger scam in the year 2017, many users became the prey of unwanted data sharing through keylogging. The victims received e-mail, disguised as a requested invoice which contained one password protected word file. The password was provided in the e-mail. As soon as they opened the file and added the password, the keylogger gets installed in the system. Now the spammers could get all the information about each stroke.
What you can do?
The most efficient way to avoid it is to be smart enough to avoid it. However, getting some precautions with technological implementations would be appreciated. Installing anti-phishing toolbar in your browser will avoid your landing upon malicious sites. These software programs could be added as extensions in the browsers. If any website looks fishy, then it will alert you and protect you against phishing scams.
If you need to visit a website necessarily even if it looks suspicious:
- Make sure that the URL of the website starts with “https.”
- A closed lock icon must be present near the address bar.
- Also, check the security certificate of that website before dealing it with.
Keyloggers could make the performance of your system slow. Also, it may happen that sometimes when you wish to enter the text, it won’t appear in the required area or perhaps there may be some time lag.
But what if you don’t need to manually add the credentials on the phishing web pages or while a keylogger is installed in your system?
There are password managers available such as LastPass, Roboform and Dashlane which automatically saves and fills the passwords instead of manually adding them. Not just this but use of robust security features are also implemented.
The passwords are encoded using through encryption and could only be obtained as plaintext by using decryption key. User authentication is also added in few password managers that if through any new website the credentials are required to be added, instead of sending the master-password hashes, a one-time password will be sent via contact information (e-mail or phone number). Only after verification of the user, the protected passwords would be obtained.
ID Theft
Imagine the situation while one is enjoying a book seating near the fireplace and suddenly police knock the door with an arrest warrant.
Identity theft occurs when a person’s personally identifiable information is obtained by an imposter to get credit, do shopping and many more. Even the identity theft could lead to the generation of criminal records with false credentials.
It could be obtained from individuals of different groups providing different benefits:
- Filing false tax return
- Medical identity theft
- Senior citizen identity theft
- Minority identity theft
- Children identity theft
And one will come to know that his identity has been stolen when he realizes that the benefits which he requires to utilize are already used by someone else. After that, he may notice unknown bank withdrawals, lower credit score, rejection from the health plan, etc.
Example
A lady with the name Margot Somerville was arrested and was accused of defrauding several banks. Later it was discovered that the real criminal was Harris-Frazier who used Margot’s identity to commit these acts who was caught after the discovery. Tens of thousands of dollars were obtained with his fraudulent actions.
Such incidents could even take place on a large-scale when someone obtains the information such as driving license breaching through the government security. After that, this information could be sold, and different people could mask the identity of the person whose driving license was obtained.
What you can do?
Precautions are the best solution. However, sometimes ID theft could occur even after our careful check over the credit report and banking transactions. One can’t monitor the use of personal data over the internet 24/7. Also, it’s tough to identify that from where the data trading had occurred.
That’s why identity-protecting services are utilized by many of the users that let the user be carefree about the data. It monitors and notifies you at the same time whenever the trade occurs. They keep track of usage of Social Security Number, monitor your PII over the dark web, give alerts on bank and credit card activity and provides lost wallet protection.
LikeLock and IdentityForce are some prominent services on which rely for safeguarding PII. These identity theft safeguarding services also help the individual to recover from the effects caused due to data theft by providing stolen funds Reimbursement. Also, they also cover the legal fees and provide personal expense compensation.
However, if the exchange and the usage of ID theft occur offline, it may not be easy to track it down.
Spyware & Malware
It’s similar to someone keeping an eye on one’s house and knowing everything about what’s going on inside it. It will know about every activity that one performs on his system and collect the data and transfer it to another entity which could use this data for personal gains. They are also used to monitor one’s activity over the Internet, and then it shows ads according to that. It could be harmless in many cases; however, it’s not good to take the chance.
There could a possibility that cyber-criminals not only wish to keep track of your activity but also wishes to damage or get unauthorized access to your system. In that case, they would get malware installed in the system without your knowledge.
Example
In the year 2017, the Israeli soldiers became the prey of spyware which was downloaded through the Google Play store in the form of a genuine application. That wasn’t direct, but the hackers impersonated as young women who lured the soldiers and made them download one application through a link.
In total, 100 android devices were compromised, and total 9000 files including photos, audio, and sensitive information were obtained. The hackers generate the command for searching and stealing official documents. This had also questioned the national security of Israel.
Malware is all around, helping to degrade the system’s health.
In the year 1988, the first large-scale malware attack (Morris Worm) was conducted. It spread through the internet on a very fast phase and harmed most of the systems all over the United States including devices used at military locations and medical research institution. However, the privacy was not breached, the systems became severely slow.
What you can do?
There are hundreds of anti-spyware and anti-malware products available ready to get installed. However, it’s essential to identify that what kind of anti-malware software program would be beneficial.
Spyware software programs are also available as parental control tools and are commercially available such as Spyzie. However, they are not installed through malicious links but like any other software. This kind of software programs can’t be removed using anti-spyware because anti-spyware works with the rules set according to the download methodologies. Anti-Spyware software programs such as SuperAntiSpyware & Spybot prevent unwanted downloads that may install spyware. Also, if any software is already installed, they will identify them and remove them efficiently.
Similarly, in the case of malware programs, malware detection is done in three ways:
- Signature-based malware detection
- Behavior-based malware detection
- Sandboxing
Signature-based malware detection only detects the previously known malware programs by matching the hash function. For detecting unknown malware, behavior-based malware detection and Sandboxing could be used. Sandboxing is more efficient than the other method. Malwarebytes is one such anti-malware software program which offers such methodology and also offers application hardening that crushes the hidden malware.
One can even purchase Internet security suites which provide the solution for both spyware and malware. It would also save your device from other threats which we are going to discuss further.
Ransomware
We would have categorized ransomware as malware, but this malicious software program has earned a significant level of lousy reputation when it comes to compromising data security. And so, it was essential to discuss it particularly.
One pleasant morning could turn into a bad one as soon as one opens his system and finds the message: “Your data has been encrypted, and for decrypting it, you need to pay the amount asked or else your files will be lost forever.” Ransomware encrypts your data, and for the deciphering it, one needs to pay the amount asked.
These files could be related to a project on which one was working for months, or it may contain memories that one considers his lifetime earnings. Now, one doesn’t have an option, but to pay the amount. Usually, the transaction is done in exchange for Bitcoins so that no one else could track the entity that has runs and maintains this ransomware.
Example
CryptoLocker was one such ransomware which infected 250,000 systems during the ending months of 2013. The ransomware collected an amount of $3 million that year but didn’t provide the data to everyone. The asymmetric encryption is used to lock the data which relies on two different keys. The hacker uses the public key to encrypt the data, and for decrypting it, a private key is required. However, this ransomware has not targeted MacOS.
Another severe attack took place in May 2017: WannaCry ransomware attack which had infected 200,000 systems across 150 countries. It is believed that the attack was originated in North Korea. Again, in the year 2018, it infected ten thousand machines of Taiwan Semiconductor Manufacturing Company causing its shut down temporarily.
What you can do?
One simple solution is creating a backup for every record stored in the system. However, this may save you from paying the ransom asked in exchange for the data, but it won’t save your data from hackers who may sell the information on the dark web which could lead to identity theft.
An efficient anti-ransomware product such as Hitmanpro.Alert is required to stop the ransomware from encrypting the data. It works on the behavior-tracking methodology that doesn’t track down the activity of malicious software. It creates a backup of those files before the ransomware could encrypt it. If ransomware doesn’t stop targeting the other files, the software stops it by understanding the motion and behavior.
Efficient ransomware should not only be capable of detecting the known ransomware programs but should also have the ability to track and catch the new variants.
Mobile Applications
Mobile applications are one of the biggest sources of data collection. It occurs as the individual allows the data collection by providing permission for accessing several features of the device. Not only the access but also the permission to make the changes is provided. Sometimes, it’s genuine, but a few applications could take advantage of this permission. However, apart from this, there are a few more threats which make the mobile applications vulnerable to data breaching. Also, there could be a possibility that the applications are spyware or malware in disguise. It’s not only about the privacy breach through the application but also questions the security provided.
Example
Thirteen malicious applications were detected which were hiding in Play Store under the developer name Luiz Pinto. Out of these thirteen apps, two applications even made their way to the trending section. Altogether there were 560,000 installations because of which these devices got affected by the malware, which let the cyber-criminals have unauthorized access to these devices.
Applications such as Truecaller, Hiya, CallApp and Whoscall are collecting a huge amount of contacts related data from our mobile devices. Truecaller for example collects the data from our devices, and we let them show the contact information to other users at the time of messaging and calling. This is serious breaching the privacy of the contact which is saved in our device. However, it’s not the main concern.
The main concern is when data breaches occur, and databases of such application get stolen. The hackers could get their hands on the contact information of millions of users which would make the users’ privacy vulnerable.
What you can do?
Before you download an application, make sure that:
- Application has the minimum third-party involvement.
- Provides binary protection so that no cyber-criminal could regenerate the application or sell a pirated version implemented with the threat.
- It is available on the app store and approved by the respective company that owns the store.
- They use high-security encryption for the source code so that no one could identify the vulnerabilities present in the code.
- Do not download the application from outside Application Stores.
- Avoid permitting access to feature the application asks if it is not required at that time.
Search Engine Tracking
Google knows who you are, where you are, what you search for, what you like and what you would like. Whatever we do over the internet using the search engine is recorded by the respective search engine. The search result varies from person to person according to location and previous searches. However, the data sharing is done with our permission, and it has its advantages as well as disadvantages.
Example
Advantage: If you are searching for the best doctors, it would be useless to you if you are in Chicago and the result shows doctors available in London. The search engine utilizes the location shared and shows the result for the doctors around you.
Disadvantage: For a holiday planning or for just satisfying the curiosity, one searches for hotels and restaurants at Hawaii. However, even after he closes the tab, it keeps showing the related advertisements on the other web pages. It could be annoying, and at the same time, it may lure one to make a wrong deal.
Now if we consider a case where we type “Dog Training” in the search box of a search engine, the results will appear. Now if the next search consists of any keyword placed before the “dog training,” it will automatically show it without typing again. Let’s say, you type “how to” and then it will show suggestion related to it: “How to train a dog,” “How to become a dog trainer,” etc. This shows the capability of the search engine to remember the previous searches. For some this may be a better user experience but you can imagine how even little data is used by these corporations and can adversely affect your privacy if you logged in and saved your search history.
What you can do?
Using incognito has always been helpful to avoid tracking. Even though, whatever one searches gets recorded in the search engine’s database, it won’t show any relevant or irrelevant advertisement that has anything to do with your search history. Also, it won’t show suggestions according to the previous searches.
Showing relevant suggestions could be beneficial, but again it may harm one’s privacy. If one is concerned about the search engine tracking, he must not log in to the browser and the search engine. Logging in will create a profile which would contain your daily searches according to which one show advertisements and suggestion.
DuckDuckGo appears as a privacy savior who doesn’t create a profile of their users and does not change the search results according to the previous keywords typed by the user. However, the show advertisement based on the “current keyword search.” The filter of personalized search is removed, and it focuses on providing the best result rather than showing the link which is used the most.
One can also use Search Encrypt which encrypts the data locally using AES 256-bit key encryption. Even if it checks the URL that you visit, it claims to have no data logging policy. After transmitting the data to the servers, the decryption takes place, and it’s search partners shows the result according to the keyword.
Website Data Collection
Data could be collected voluntarily or through data trackers which work in the website background. The data recorded could be sold or rented to the third-parties. Even though, if you visit a website and conduct minimal activity, then also some of your information is collected. This could also be done for the website’s improvement by identifying the users’ behavior. However, it could also be harmful if any hackers get their hands on any sensitive data which we would have shared with the website for the betterment of our own experience with the website.
Voluntarily Provided Data
- Information provided during sign up such as e-mail address, name, date of birth and country.
- Payment method added to the website while making a purchase.
- Searches made over the website according to requirements and likings and collecting them in history.
- Location Sharing whenever required such as in food delivery and cab services.
- Adding onymous comments providing your views along with your identity.
Data Collected Through Trackers
- Tracking your IP address.
- Device from which you are logged in to the system.
- The time you spent on a webpage.
- HTTP referrer which lets the website know that from which external link you have come to the current web page.
- The user agent which allows the website to detect the operating system and browser which user is using.
- Cookies such as credentials or changes made in the settings.
Web tracking is beneficial not only for the website but also for the user. However, when third-party trackers are involved the data tracking could become harmful. Whenever you visit a website, it logs your visit on its website and for the particular web pages that you come across. However, if another website is embedded with it, it will also be allowed to keep your logs, and that could be done to identify your interests. This information act as a helping hand for online marketing and advertising.
Example
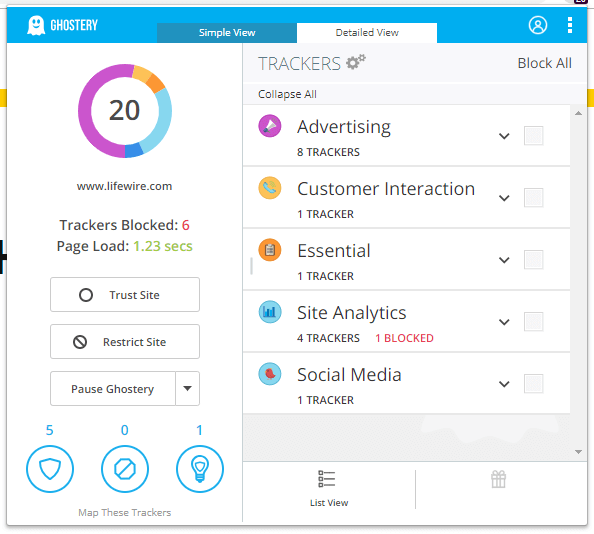
For different websites, different trackers were established which work in the background. We visited one website that has twenty-four trackers working in the background which were provided in five different categories:
- Site Analysis
- Advertising
- Customer Interaction
- Essential
- Social Media
Site Analysis trackers are required to improve the performance of the website. Tracker such as ScoreCard Research Beacon monitors the behavior of the user by finding visiting patterns. Catchpoint renders end to end real-time analysis which lets the website have the details of internet service through different aspects.
However, Trackers such as Amazon Associates and Facebook Customer Audience keep the logs which helps them the third-parties to market and sell their product by understanding the user behavior pattern.
So, whenever the third-parties are involved, the data tracking could be harmful even if it doesn’t expose your PII.
In the case of data breach just as in happened in the case of Google Plus, the email, and the name of 500,000 users were exposed even though they were private. Sharing these kinds of information could be harmful and must be done in a limited way.
What you can do?
Ghostery is an efficient anti-tracking device which not only tracks down the tracker but also informs the user about it along with the description. You could block all the trackers or a few according to the privacy that you require. Site analysis trackers are beneficial for the users and websites, so it is suggested not to block them. However, you must block the trackers which provide your information to the third-parties that use it for advertisement and marketing.
Make sure that the website that you are visiting is genuine and has an SSL certificate. SSL certificate lets the user have an encrypted communication and whatever data is exchanged between the website and browser will be protected with a layer of security.
Also, instead of providing payment information, you can add anonymous payment methods such as Bitcoin which would help to safeguard your identity.
Ads and Retargeting
Advertisements provided to you comes from the cookies and supercookies which are collected by the websites. Also, the tracker which we have mentioned in the previous section plays an important role in targeting the audience.
A search engine such as Google also shows advertisements based on your history as their algorithm suggests your interest in a particular product.
In the case of retargeting, websites add a javascript in the footer which collects the information about the user behavior. Whenever the user visits the website again, the website would know because of the cookies placed in your system anonymously. The advertisements will appear again which helps them to convert the window shoppers into customers.
In the case of supercookies, they get permanently installed in the users’ systems using HTML5 web storage which can’t be removed like the regular cookies.
Example
Whenever you visit a website such as Amazon and do some searches related to various products, it would show relevant results and store the behavior in the form of cookies. This one can remove directly through the browsers. If not deleted, whenever one visits the website again, they will retarget the items under a particular section such as, “Products that you would like,” or “Related to your products you have viewed.” This helps to catch the attention of the potential buyer.
Even if you clear cookies, if you are logged in to the account, Amazon would make a profile of your searches and target and retarget the products accordingly.
As we have mentioned in the search engine tracking also, Google could target the advertisements based on your history and previous searches.
What you can do?
Clear cookies would be first and using ad blocker would be another. There are inbuilt settings in the browsers related to the content that the websites can track. You can always disable the content that you don’t wish to share with websites. However, some websites may not allow you its access.
In that case, one can install the adblocker extension which may help them to avoid certain advertisements. However, it won’t provide a solution to retargeting.
Even if you clear the cookies, super cookies aren’t easy to detect and get rid of.
These cookies could be detected using Adobe Flash Player settings manager where you can find a list of flash cookies which is a type of supercookies. From here, one can easily delete them all and to prevent any new addition of flash cookies in the system Global Setting could be used. Set the “size of data that a website is allowed to store in your disk space” to none and checkmark never ask again.
Social Media & Behavioral Targeting
Social media platforms are the best data sources for the hackers as they provide not only PII but also the sensitive data generate through messengers and timeline. One can detect the likings and mindset of a user just by detecting his timeline activity. The social media platform itself detects the users’ interests and show advertisements and page promotions to those users.
However, more than this, access to messengers, sensitive media and text could be obtained; the cybercriminals could publish and sell the data.
Example
Yes, what’s the first name appeared in one’s mind? “Facebook?”
It must be the one because who would forget about the news about Cambridge Analytica Scandal that came out in the year 2018. Information about 87 million people (according to Facebook) was collected from Facebook including timeline feed and messages of some of the users.
One more Facebook attribute, Facebook Graph Search makes the user more discoverable over this social media website. This search engine lets the different searches combine to provide results related to the people; one is looking for. Such as the search “people living in Berlin who have visited France” will provide information about a specific crowd showing them as the search results.
Not just Facebook, but also the social media websites such as Google Plus and Twitter have faced data breaches concluding that it isn’t safe to use these websites.
What you can do?
To be anonymous is the best way to remain hidden. The more data you share, easier to track your activity.
Limiting the data share using the privacy setting can help to limit the control of other users over your information. However, level of privacy varies with person to person, and so the sharing options could be changed accordingly.
- Who can connect with you: No one, Friends of Friends, Anyone.
- Who can see your contact information: No one, Friends of Friends, Anyone.
- Who can discover your timeline content: No one, Friends of Friends, Anyone.
Such general privacy settings could be set according to the requirement of privacy. However, it is still suggested that not much information should be shared through which one can stack and identify your details. We would never know the intentions, and it may lead to personal effects of data breaching. In the case of children, social media acts as a catalyst for child trafficking and sextortion about which you can read it in our child privacy guide.
GPS and Navigational Data
Services such as Google Maps and Foursquare efficiently track your location. It’s useful on our side which helps us to know where we are or how to reach the destination. These applications even tell about the best path, about its traffic and the time that is required to reach there.
Also, the websites such as Facebook and Instagram, use your location when you wish to add a check-in to a city, restaurant or any other place.
This data could be used to create a profile which contains the location history knowing that what places you visit the most and where you have been.
Example
Google Maps is used by a vast number of users all over the world. Google knows how many devices are present at a certain position. With the help of that, traffic rate over any path could be recorded. That helps the users to provide the accurate details that what amount of traffic he is going to face. That’s not a threat, but on a personal level, it logs whichever place you visit.
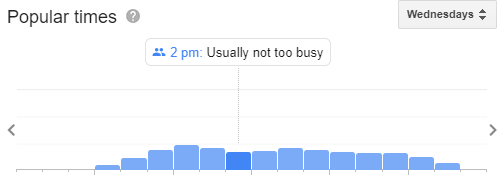
It’s not just about the present location tracking they create, but also with the help of predictions. The machine learning features help to detect the density of the traffic that the user is going to face since traffic present on the road every day. Everyday data is collected and added which improves the prediction and provides accurate results.
Google also provides information about the real-time busyness of a particular place, and that information is obtained through smartphones. The device location, even the location sharing is switched off, is provided to Google which they could use under the “Popular Times” section of any business.
What you can do?
Location sharing must be provided only when required the most. In the case of applications which require a location for check-in details, sharing must be avoided as it provides real-time information of the location publicly.
Using dedicated GPS navigation devices such as Garmin which doesn’t require to build your profile or keep logs for your data, one can safeguard his privacy. Even if it keeps logs, it won’t be knowing about the person who is utilizing the device as it doesn’t require any sign-up. Also, it works without cellular data, so no chance of getting tracked by any third party.
However, privacy comes with a cost, and you won’t be able to find out the traffic which was provided by other navigational applications.
Through Browser
Browsers are the gateway to the internet and every activity we perform over the internet could be recorded by the browser. Every web page one visits are recorded as “History” by the browser. History acts as a track record that could be deleted from the device. However, one can’t delete the track record that the browser provides to the website that one visits. Every device has a unique fingerprint that is generated according to the browser settings, but if one doesn’t allow exposing the data more than the required data, identification of his device could be difficult.
Example
If you go through Chrome’s privacy settings, you will find content settings in which access to different features is asked. Here, you can disable the cookies so that the browser doesn’t let the website save any data and read it afterward. You can also control the use of javascript through it. However, it was found inefficient for many websites. Even after changing the settings, the Chrome allowed appearing of pop-ups and redirects. So, it could not be clear if it’s reliable for privacy or not.
What you can do?
The only solution to it is to use the browsers such as Tor and Epic browser. Epic browser claims to block ads, data trackers, fingerprinting without logging any of the user data. Even the URLs can’t be visited through the search history as they aren’t recorded at all.
Tor is the most anonymous browser which is not owned by any business but runs and is maintained by a group of volunteers all over the world who are volunteering for the Tor project. When one starts using Tor, no information about the user could be revealed. However, if one starts purchasing goods or provides credentials by logging in any website one’s anonymity will decrease. Tor also works on the encryption methodology in which not only one, but three levels of encryption are used.
ISPs and Government Spying
Due to data retention laws present in many of the countries, ISPs require to keep track of user’s activities. Whenever the government requires the data for investigation, they can access it through ISPs.
But not just this!
ISPs could even sell the data generated by tracking the user to the advertising companies which are ready to pay a high price for it. That helps these companies to direct their products to the correct audience.
You would have experienced lowering down of your internet speed even if the weather is clean and the router is working fine. The reason behind this is bandwidth throttling (intentional lowering down of speed by ISP). That may not be related to privacy. However, allowing one to keep track of bandwidth usage would be harmful.
What information can the government agencies could obtain about any citizen
- His current location and location history.
- His credentials of any social media website.
- The financial details and purchase history.
- Call logs and messages.
- & pretty much everything including the information that he would not have shared with anyone else.
Surveillance programs such as PRISM conducted by government agencies such as NSA had breached into the privacy of every citizen.
One could stay protected from the malicious programs by taking protective measures. Careful use of different online platforms will ensure the security from the data breaches through the website. However, when the government is the one who is tracking the data, it could be difficult and, more important to hide the information.
Examples
Chinese government with the use of “Great Firewall of China” regulates the domestic internet. Because of that most of the foreign websites have been blocked and exchange of international data has been decreased.
Under this program, certain IP addresses are blocked and not allowed to be accessed, even the URLs have been filtered, and if every individual is monitored for continuously and if access of any restricted website is done, someone could be charged for that.
Privacy could be compromised not just by the monitoring the data but also by hacking of systems without any fear of the law. NSA was divided into three different categories:
- GAO division: Responsible for the collection of overseas data.
- SSO division: Responsible for the collection of domestic data.
- TAO division: Responsible for collecting data through hacking operations.
The intelligence agencies which are similar to NSA are present are all over the world; for example, New Zealand’s NZSIS and Canada’s CSIS were found outsourcing citizen surveillance data to partner agencies.
What you can do?
The Virtual private network separates one’s data with the data presented over the Internet. This data that is transmitted over VPN works on the principle of encryption. The plaintext that the user enters is changed into ciphertext with the help of VPN client. Then the data travels through a secure tunnel which is generally not detectable.
Also, different servers of VPN providers present all over the world changes the location of the user which helps the user to access the geo-restricted content and also blocks the unauthorized access of the websites which tend to track the location of the user. Even the ISP won’t be knowing your true location and the websites you visit will also remain hidden.
For Chinese user, Stealth VPN protocol is developed that mixes with the standard internet traffic and doesn’t allow one to detect the use of the virtual private network
Public Wi-Fi
Wi-Fi, it’s vulnerable if anyone is allowed to connect with it. Wi-Fi network provided at coffee shops and libraries allow anyone to connect with it. In that way, anyone can see that which are the other devices utilizing the same Wi-Fi connection.
Not only this, but it’s also easy to breach through anyone’s device if he is using the same Wi-Fi that the hacker is using. Applications such as zANTI which is a penetration testing toolkit is a hacker’s best friend. By using the Metasploit framework, one can exploit the vulnerabilities present in networks.
Example
Israel’s second most populous city, Tel Aviv had its Wi-Fi network hacked by the hacker name Amihai Neiderman. He hacked the Wi-Fi our of curiosity to check how secure it is. It just took him three days to perform this task.
First, he found out the IP address of the router to which he was connected. He looked for the open ports and found one. All he required to do is to discover the vulnerabilities for taking the complete control over the internet. For that, he tried to find vulnerabilities in a different version of the same framework which provides lesser protection. He discovered a vulnerability which was also present in this version.
By that, he took control over the Wi-Fi to which the users of the whole city were connected.
What you can do?
It’s important to make sure that these passwords should not be broken through brute force. That makes it a lot easier for the hacker to bypass the password just by a technique of placing combinations. To avoid this, one must use a strong password which consists of alphabets, numbers, and symbols.
The above example shows how important it is to encrypt the data so that no one could get it. For that, a private network is required. Inside the public networks, a tunnel could be created which would provide a layer of security using VPN clients. The data inside the tunnel is secured by encryption, and so, it could be obtained directly
Reverse Search and Background Check
Nowadays, it’s easy to identify and find every piece of information about someone just by one piece. There are several search engines available which allow their users to conduct a reverse search, i.e., by knowing one thing about the person, you can shortlist a group of people who are having that data common.
And if you find something unique about the person such as phone number or the vehicle number, you can get the complete information about him by just paying a few bucks.
Example
Reverse search websites such as pipl.com and spokeo.com are available to everyone. In both the cases, all you need to provide is one piece of information out of these: name, e-mail or phone number. You can get the complete record of the people who are having that the data that you have entered associated with their identity.
In the case of Spokeo, one can even get the results by entering the addresses. Even if it doesn’t provide the exact information in some cases, it can at least give information about the people living in that particular area.
Intelius is one of the top websites which provide background check service. No one exactly knows that from where they acquire the data, but there are possibilities that they are getting it from the government records.
What you can do?
Well, frankly it doesn’t depend upon you completely, and it matters a lot that how the government of your country is safeguarding the details.
After these identity search websites get your data, you can opt out by contacting them. However, this is the tough part which may require you opt-out forms and send identity confirmations
Personal Health Records
If one visits the dark-web, he may come across his medical history for sale.
From where the dark-web got the access to these Files?
Perhaps, from the medical entity with whom one would have shared the data for treatment.
These medical organizations may or may not have shared this data knowingly. There are many medical bodies where a data breach has taken place because of poor security or due to hacking. Sometimes, it is done with the help of someone who could get access to the information. So, it is a complete gamble to rely on any medical entity. Till now, if we add up all the significant data breaches, in total, approximately 165 million records were breached since the year 2004.
The fear is not only of data breaching but what if someone corrupts one’s medical reports by using them for himself? The information in the medical report won’t be the same, and it could lead to misdiagnosis.
Example
The biggest data breach occurred when hackers obtained Anthem Inc.’s 80 million (According to the NewYork Times) records. The data contains personally identifiable information, even containing the medical IDs and income to the person. That data would have been sold on the dark websites. The people whose data was stolen may suffer issues related to identity theft. One disappointing but interesting fact about this breach is that during the investigation it was revealed that it was started with a phishing e-mail.
What you can do?
Treating your medical data as the financial data is the only way by which you can carefully take charge of safeguarding it. Like you don’t reveal everything about your financial details so, only let anyone know what’s necessary in the case of medical details also.
Reviewing the medical records time to time is necessary because here the fear is not only about the breaching but also of misdiagnosis. Keeping a check on the medical data may reveal the changes which are made by the hackers, and then one can take actions accordingly
CCTV and Webcams
Closed circuit television is one of the prominent ways by which one can keep his eyes on a specific place. It has many uses such as traffic monitoring, sports events, and crime prevention. If any breach occurs, the video could be altered even without the knowledge of the authority handing it.
Websites such as earthcam.com and skylinewebcams.com show the live view of several public locations. These could be a purpose of security as well as entertainment to have a look over the places which are visited by thousands of people daily. However, this could affect the privacy of the person who has been watched through the camera. Also, he doesn’t have an option to opt out if he visits the place.
The information remains with the respective websites, but if the breach occurs, a huge amount of personal data such as the location of a specific person at a specific place would be obtained by the hackers.
Not only public, but the threats are also to private CCTV cameras which one uses as a home security tool. With that, the cyber-criminals could keep an eye over you tracking your every activity. This may contain sensitive information which one would not like to become public. The cyber-criminals could affect one physically and emotionally by conducting criminal activities such as blackmail.
If those cyber-criminals get into your systems, there are even chances that they conduct Camfecting, and keep an eye on someone through it. This is generally done using by sending a Trojan software disguised as an innocent-looking application. After it gets installed, every second of the victim’s activity gets recorded and sent through the webcam.
Example
In the year 2017, Romanian hackers were looking to have some fun by hacking Washington’s surveillance cameras. Out of one hundred eighty-seven cameras, they took over one hundred twenty-three cameras which disturbed the security system of the city. This was done using spam e-mails which were infected by ransomware. For three days, all the cameras were taken offline, after which software was removed and then reinstalled again.
Website with the name insecam.com claims that it has hacked thousands of private cameras placed at shops, homes, farms, etc. On the website, one may find the category option by which he can stream the cameras of several locations according to the person’s choice. This is very dangerous as they have access to every activity, and also shows the description containing information about the activity, device used, and location of the camera.
Macpatcher’s Youtube channel became popular with the testimonials they received in the exchange of service they provided. However, the service was fake, and the video testimonials were recorded without the knowledge of the user. They convinced the victim that there’s a virus installed in the system, and it could only be removed if they remotely access the device. As they get the remote access of the system, it lets the spammers to turn on the webcam. They ask the victim to read the script which they record without the user’s knowledge. These videos were afterward used as testimonials for gaining the attention of more and more users.
What you can do?
The most important step is to purchase the right security camera. There are two types of security cameras present: IP and analog, which are used for small-scale as well as large-scale purposes. Even though IP security cameras have better image quality and are easily manageable; they are more vulnerable to breaches. In analog security camera, the data is transmitted in analog form using coaxial cables. Hacking through it would be a tough game, so if one wishes to setup small security surveillance for small shops or home, they can consider using it.
However, for the large-scale requirement, one needs to use IP cameras which are vulnerable to breaches. Generally, breaching takes place by bypassing the dedicated network’s security or through the device by which cameras are remotely accessed. For avoiding it, using cameras which sends data in the form of encrypted signals would be the best option.
Some precautions such as changing the password in short time intervals and keeping track of logins would safeguard or at least make you aware if any breach occurs.
Regarding webcams, one must not allow downloading of any unrecognized software. Generally, the hacking takes place with the help of Trojan software programs. There are dedicated webcam protection software programs such as Secure Webcam and Webcam Protector which detects if the webcam gets enabled or if someone is accessing it remotely.
Breaching through Email Communication
E-mail communication is the traditional electronic medium for communication which is the simplest, fastest, but the most insecure way of communication. Breaching may occur while the email is in transit, saved in the users’ system or stored in the email servers. There could be legal breaching also by the company itself which stores all the information that it gets through the emails that we send or receive.
Examples
Illegal Breaching: It has happened with the politicians such as George H.W. Bush, Sarah Palin and Rowenna Davis which shows that even with high security, it is not impossible to breach someone’s email. On a larger scale News of the World has hacked several emails of famous and infamous personalities using spyware. In total, a six-figure settlement was provided officially to the victims whose email accounts were hacked. Other than this, many more settlements had been taken place between the victims and the news channel.
Legal Breaching: Gmail uses the content which we share through email for retargeting advertisements. Perhaps, this could be done by finding the keyword and matching it with the keywords associated with the advertisement. That’s how the company knows that what kind of data is getting shared.
What you can do?
Sending the data in the form of encrypted messages could be the easiest solution. However, it isn’t time efficient and requires additional efforts. Email tracking option helps you to identify if the email has been read by someone. You can download Google Chrome extension: “Email Tracker” which works for Gmail, Yahoo, and Hotmail. That will let you know if any third-party gets the access to the email. Apart from that Keeping, a strong password would be helpful to avoid the breach through brute force.
Devastating Effects of Privacy Breach
Financial Loses
Stolen data could affect a company as well as an individual financially. If the financial accounts are compromised due to breaching through the account information such as debit card and credit card details, it may be misused by the hackers.
If the data breach occurs by trespassing into an individual’s system, only he will get affected. On the other hand, if that happens by breaching into an entity that stores payment information of several individuals, then all the users may get affected with it, and large-scale financial loss could be expected.
If a data breach occurs, then the decrement in the company’s reputation could lead to a reduction in share prices. Even the loss that occurs due to the data breach may be insignificant when it is compared with the loss due to the damaged reputation. Because of the loss of confidence in the company, everybody starts selling the shares at lower prices in fear of the collapse of the company. The net worth of company decreases, and it may take years to regain the stability.
Personal Threats
No one would care about anyone’s photographs or other media files, call records or messages till the time when they could generate any kind of profit from that. Such data leakages always attack the personal life of the person. It often becomes a way of blackmailing and hackers gets a handsome pay to keep the documents secret. However, it’s not sure that they would keep the documents secret or not even after the payment.
If a hacker learns about someone and starts tracking him, criminal activities could also take place. Information about a child could act as a catalyst in helping the criminals to commit crimes such as child trafficking and kidnapping. It may also make the security of other family members vulnerable would already know about their every activity.
Data Abuse
One can’t make sure that if his data is available on the dark web unless he is using any ID theft guarding service. There could be thousands of data breaches that would have gone undetectable. Through these data breaches, hackers would be making millions by providing information about millions of people. On the dark-web, the information is categorized according to location, gender, age, nationality, etc., and sold over different data selling websites.
Dark-web makes it much easier for cybercriminals to perform phishing campaigns. This is done with the help of a phishing kit containing phishing website resources. All the work that attackers need to do is to get the email list of potential “phishes” which is also available on the dark-web and send them the e-mail. These spammers continue the breaching chain through the fraudulent acts that they do through varies means of communication.
Impact on the Society
This might have happened when Cambridge Analytica was executing research over the personal data of 87 million Facebook accounts. One must not forget that Cambridge Analytica is the data analysis company which was executing Trump’s election campaign. With the help of data mining of personal information, a digital copy of a person’s phycology could be created, and his way of thinking could be learned. On a larger scale, how a crowd acts towards activities is categorized, and their judgment could be altered without their knowledge.
Privacy is like safeguarding a material inside the container. The container belongs to a person who doesn’t wish to reveal what’s inside it. But there are several pores in the container through which external forces try to watch that what’s inside. However, one puts multiple layers of covers to the container to safeguard it from those intruders. Here, in real-time those intruders are the government, hackers, viruses, and cyber-criminals who are trying to keep a watch over one’s data. These layers of security are of products such as VPN, Tor, Anti-Spywares, etc., which act to save one’s data from others.
Conclusion
However, it is not possible to cover every point of leakage, and a breach may occur. If one wishes to retain a hundred percent privacy, one must keep a check over every pore from where data could be leaked. Take all the necessary steps and never compromise to invest or to act in the favor privacy.
Well, if something belongs to you, its worthy to make attempts to secure it from others.
