Pros

- Swiss Jurisdiction: The service is based in Switzerland, and all of us know how strict the Swiss laws are when it comes to privacy. The jurisdiction does not mandate businesses to collect personal information of their customers and supports minimal data collection.
- No-Logs: As the name suggests, Perfect Privacy follows a stern no logs policy. They don’t collect any personal information about the users while using the service. They do not even collect the time stamps.
- Strong Encryption: The service comes with 256-bit encryption, which is the most robust encryption available right now.
- NeuroRouting: This is one of their exclusive features which uses artificial intelligence and machine learning to keep the internet traffic under the VPN blanket for as long as possible.
- TrackStop: This is an ad-blocker which comes along with the VPN product. Along with blocking all the unnecessary and sometimes harmful ads, it also provides a lot of customization options to the user. It includes parental control, and the user can block fake news as well with its help.
- Multiple-level kill-switch: They have provided a three mode kill switch which will keep the user’s data safe by stopping the internet traffic in case the VPN connection drops or even if the user forgot to turn on the VPN altogether.
- Cascading: With this feature, the user can connect to a maximum of four VPN servers at the same time. This increases the layers of VPN cover for the user’s internet traffic, and he/she can feel more confident about online privacy and security.
- IPv6 leak protection: The client supports IPv6 on most of the servers, and also mentions which servers support IPv6 in the server list as well. This will prevent any possible leaks because of the IP mismatch.
- Warrant Canary Statement: The service also maintains a warrant canary statement which is updated every month. The user can feel even safer knowing that the company is not facing any kind of legal implications.
- Stealth VPN: With Stealth VPN the user can bypass various firewalls installed by multiple governments and institutions. Stealth VPN disguises the VPN data packets as the usual data packets, circumvents the firewalls.
Cons
- Few Protocols: The client comes with only two protocols, that is, OpenVPN and IPSec. With so many protocols available these days, they can include a few more for sure.
- No server sorting: There is no server sorting on the service, and they have not provided any dedicated servers for streaming. However, they display the current bandwidth usage for every server.
- No chat support: There is no live chat support available on the service. Live chat supports help a lot when the user is new to the product and enhances the user experience.
Overview
Perfect privacy is a decade old VPN service which is owned by Vectura Datamangement Limited. The company is based in Switzerland.
| Quick Overview | |
|---|---|
| Protocols | OpenVPN, IPSec, SSH2-Tunnels, PPTP |
| Platforms | Windows, Android, Mac, iOS, Linux |
| Jurisdiction | Switzerland |
| Logging | No logs |
| Encryption | 256 AES |
| Connections | Multiple Connections |
| Locations | 23 Countries |
| Servers | 37 |
| Payment Options | Paymentwall, PayPal, Bitcoin |
| Support Options | Ticket Support |
| Pricing From | $ 9.99/mo Billed for 12 months |
| Guarantee | 7 Day Money Back |
| Website | Visit Website |
Switzerland is famous not only for the beautiful mountainous landscapes but also for the strict privacy laws in the country.
The local laws don’t make the enterprises and services store the personal data of their customers and users. The jurisdiction is ‘Perfect’ to safeguard the ‘Privacy’ of the users.
The product seems to have all the necessary features required of a good VPN service, and then there are some advanced features on top of that as well.
The first thing we noticed about the product is that it is loaded with features. Some of the features are relatively new and technologically advanced, while some of them are the traditional VPN features with a few scaled-up properties.
The security on the service seems immensely fortified, and there are so many ways to keep the user safe from the harmful elements on the internet.
They seem to be a very transparent service with a lot of emphasis on keeping the user as anonymous as possible. The presence of warrant canary statement and acceptance of throw away emails also reflects the same.
In this review, we will be going through all the features available on the product and scrutinize them to judge the effectiveness and the usefulness of the feature.
We will also do a thorough analysis of the privacy policy and come up with all the facts we find there.
This review will be mostly about gauging the usefulness of the various features available in the service and checking if they have been able to take maximum benefit of the strict Swiss privacy laws.
NeuroRouting
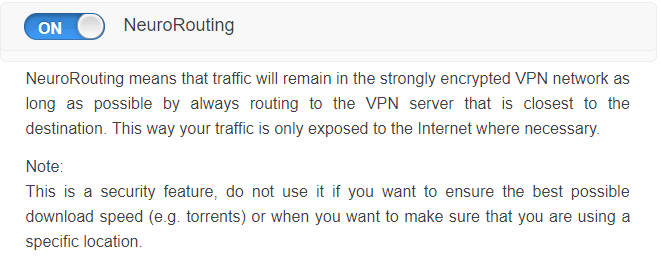
NeuroRouting is an advanced feature which is exclusive to Perfect Privacy, and we have to say that it is of the unique ones as well.
It further strengthens the security and anonymity of the user on the network. It is an artificial intelligence-based technology.
They used TensorFlow, which is Google’s opens-source library for machine learning and created a technology which continually works to find internet traffic routes to minimize the flow of traffic outside the VPN network.
This keeps the traffic data secure for most of the part of the route, and the possible ways to compromise the data reduce by a significant margin.
Let us try to understand the working of this feature. Suppose the user is in Amsterdam and wants to visit some XYZ US website. The user has manually chosen the Amsterdam server which was the closest one for his location.
The NeuroRouting will direct the traffic from the Amsterdam server to the US server within the VPN network. That US server will be chosen which will be the closest to the XYZ US server. And then from that VPN server in the US, the traffic will be finally sent to the XYZ US server.
The AI based neural network does all the computations for routing the internet traffic within the VPN connection, and constant searching of the shortest traffic routes within the VPN network.
In this method, the server’s data was under the VPN cover for most of the time, and since the network keeps analyzing the paths and continuously tries to minimize the distance between the destination server and the VPN server, it makes the security of data even more effective on the VPN.
The feature can be turned on/off according to the will of the user. The providers suggest that it should not be used while downloading large files to ensure that the user is connected to a fast Gigabit server.
The user can turn of the feature while trying to bypass the geo restrictions on various websites to ensure that he/she is connected to only the requisite server.
We personally like the feature for the use of advanced techniques which includes artificial intelligence and machine learning. And we also would like to appreciate the efforts of the Perfect Privacy team to come up with a way to enhance the security of the user’s data.
TrackStop
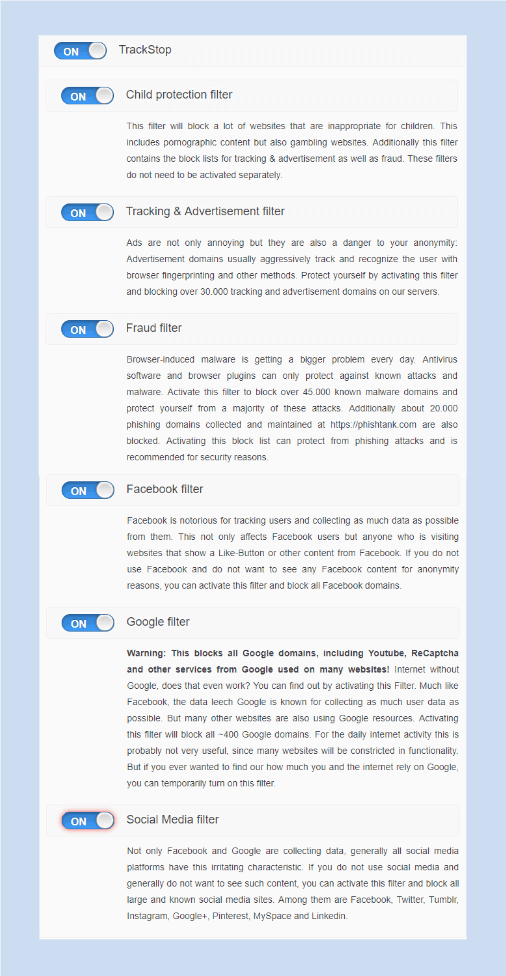
TrackStop is an ad-blocking service by Perfect Privacy. However, it does more than just a regular ad-blocker.
The user can activate it from the member area. Other than blocking the annoying ads, it also keeps the user’s device free from malware which is usually spread with the help of ad servers.
The user can add all the known phishing domains in the blocking list of TrackStop and apply parental controls to save the minors from coming across any kind of inappropriate content.
Fake news filter can be used to block content from non-reliable news websites. Another use of it is to protect your system from browser fingerprinting. In this feature, the servers will not be able to identify your browser as the same one which was using the VPN service.
TrackStop is highly customizable, and the users can add all the websites in the blocklist he/she wishes to block on the system.
Cascading
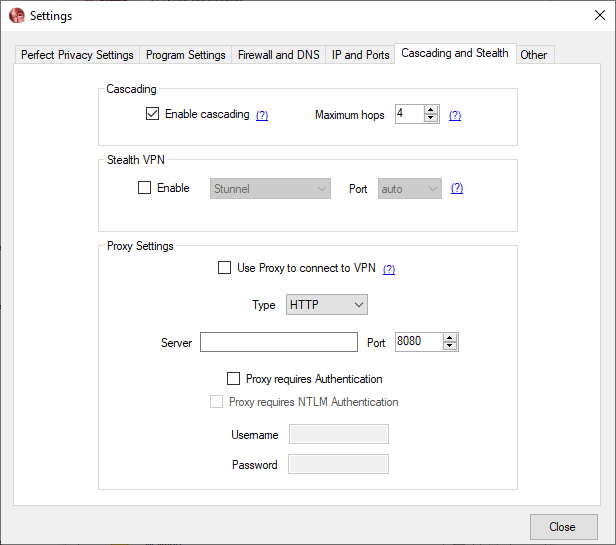
This is another one of the advanced features in this service. Even though the name is unique, the concept of this feature is not new to the VPN world.
In some VPN services this is called hopping or multi-hopping, and in some, it is called Double VPN or Multi-VPN.
The idea is to direct internet traffic through more than one VPN servers. Many services provide this facility for only of two servers, but, Perfect Privacy allows the user to route the internet traffic through a maximum of four servers.
This routing of the traffic through multiple servers, adds up the security layers of the VPN protection. However, it also slows down the internet speed to a certain extent, and that is the price one needs to pay for that extra security.
The users can enable cascading only for the OpenVPN protocol as it is not available on IPSec. The user needs to enable cascading and select the desired number of servers he/she wants to connect.
Then the user can directly connect to the VPN servers one by one on the client. The internet traffic will be routed in that order through the VPN network. Each server in the cascade connection is labelled with a number, and the numerical order gives the information of the order of the server connection.
If the user disconnects one of the servers from the cascade connection, then all the servers which follow the disconnected server in the cascade connection will also get disconnected.
Suppose out of the four servers connected in the numerical order; if you disconnect the third server, then the fourth server will also get disconnected automatically.
The user can always go to cascading if he/she wants to strengthen the security but should also be ready to face the decrease in speed after connecting to multiple VPN servers.
Most of the VPN services don’t allow the connection to so many VPN servers, and we appreciate the fact that Perfect Privacy has provided more options to the users. The feature also adds a lot of flare to the product as well.
Stealth VPN
This is one more weapon in the arsenal of Perfect Privacy.
There are a lot of countries and region where the governments deny a free internet to audiences. Most of these countries are either under communist governments or there is pseudo-democracy in the nation.
It is common to come across nation wide internet restrictions, and the government installs some strong firewalls to restrict internet in various forms.
These firewalls screen the internet data packets flowing through the region and blocks any data which they deem harmful (for themselves). These firewalls can detect encrypted data packets of the VPN services and prevent them from reaching the destination.
Stealth VPN obfuscates these VPN data packets and disguises them as normal internet traffic. In this way, the data stays encrypted as well as circumvents such restrictions.
The infamous ‘Great Firewall of China’ can also be bypassed using Stealth VPN technology. There are some countries which have restrictive internet access such as UAE, Iran, and Turkey, and Stealth can also come in handy while routing the internet traffic through these countries.
Some institutions such as universities and schools also restrict the free flow of internet, and Stealth VPN again comes to the rescue in such cases.
It will mask the VPN data packets to appear like normal HTTPS data packets and allows the user to enjoy free and unrestricted internet.
Multiple Level Kill-Switch
Kill-switch is one of the features which has become a norm for the VPN products, and all the VPN services are expected to have a kill switch these days.
But Perfect Privacy went ahead of all of them by not just one but two steps. They have provided three levels of internet kill-switch to leave no stone unturned when it comes to user-satisfaction.
An internet kill switch stops the internet traffic to prevent the user from using the internet in case there is no VPN connection. This does not allow the user to accidentally expose his/her data on the internet.
The feature is especially helpful when the VPN connection is not stable or when the user himself is a forgetful creature.
However, Perfect Privacy seems to be the first VPN service which is able to improve upon this feature as well, and they have provided three levels of the internet kill switch.
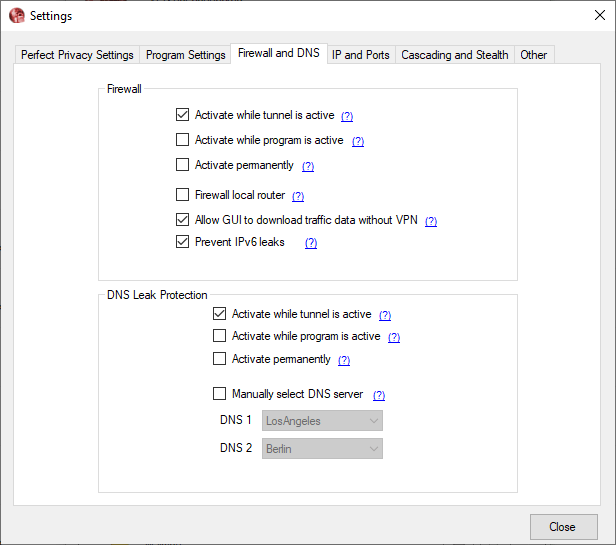
The user can switch between kill switch modes in the ‘Firewall and DNS’ tab of the settings mode.
Let us discuss all the three levels briefly.
Activate while tunnel is active:
Under this mode, the internet kill switch will be active only for the while when one of the VPN servers is connected to the internet or when the VPN connection is active.
If the VPN connection drops while one of the servers is connected, then the internet traffic will automatically stop, and the user will remain safe from the big bad world of the internet.
Activate while program is running:
This mode of the kill switch is one step ahead of the previous one, and the kill-switch will always be active if the Perfect Privacy software is running.
In this case, the user will not accidentally connect to the internet without the protection of the VPN. It will prevent the user from sending any unencrypted data over the internet.
Active permanently:
This mode is for all the extra cautious crowd out there. The ones who believe in all the conspiracy theories and don’t trust the ISPs and governments with their data.
Jokes apart, this mode makes the internet kill-switch as safe as it can get.
The kill switch will always be active, and the user will be able to use the internet service if and only if the system is connected to one of the VPN servers.
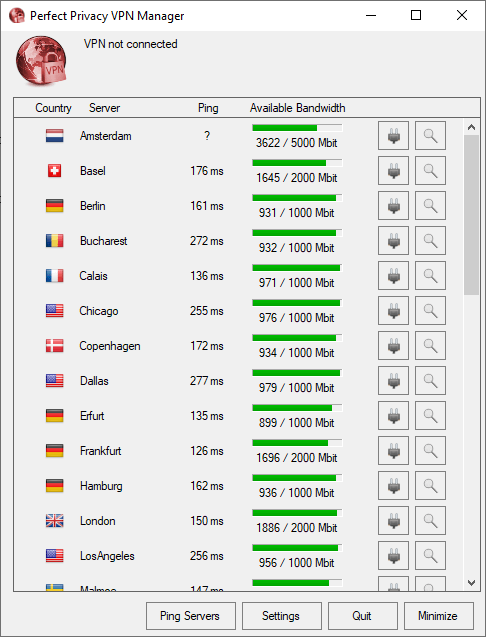
Servers
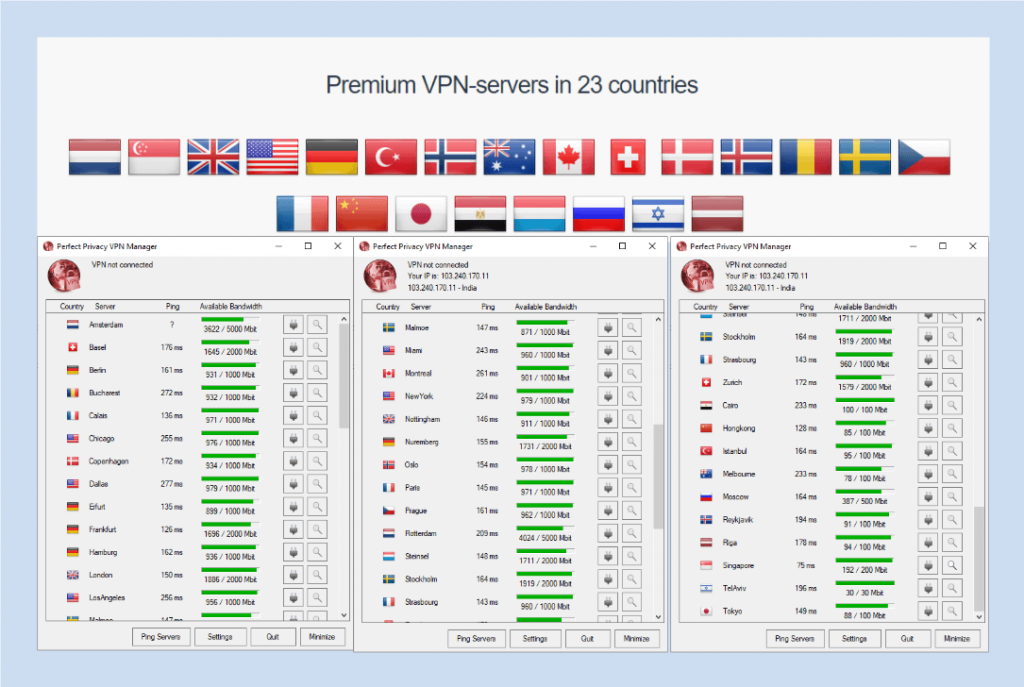
When we talk about the servers in the VPN world, having a large number is always beneficial, but it is not the only criteria to judge the service.
There are a lot of factors involved if one wants to asses the server network of a VPN service. These factors include bandwidth available, traffic density on each server, server location, physical security of the server and a lot more.
Perfect privacy has servers located across 23 different countries. Most of the server locations are in European countries.
Few in the Asian countries such as Hong Kong and Singapore, and then countries such as Istanbul and Tel Aviv are also included in the server list. The US, Canada, England, and Australia also get there fair share of servers.
The number of servers on each location varies, but the overall bandwidth available as well the bandwidth in use are displayed on the client at all times.
This helps the user to stay away from the high-density servers to avoid slow internet connections, and they can connect to the best server for them in one go.
We seldom see such features which empower the users, and Perfect Privacy has ensured that the users are not left guessing the optimum servers as is the case in most of the VPNs.
Most of the servers under the network support IPv6, and the list of servers with the information about IPv6 support is available on the official website.
Only the servers in Cairo, Istanbul, Reykjavik, and Riga don’t support IPv6 at the time of reviewing the product.
The list of features in the sever list is not over yet. Along with the bandwidth information, the client also has a ping test option available. It will throw some light on the latency of the servers, and the user can make an informed decision as he/she has got all the required tools at disposal.
Once connected, the user gets some additional information about the DNS and IP addresses. Along with this information, the user can also see the log files.
We don’t think that the provider could have gone any more into the details about the server connection.
Now let us talk about the stuff which they missed or could have added to make the product even better.
First, there are very few servers in the network. If they want to give some serious competition to the popular VPN products, they need to increase the number of servers in their VPN network.
Along with that, it will also help them if they can provide high capacity bandwidth servers across all the server locations. There is a lot of mismatch in the bandwidth capacity of the various servers at the moment.
There is no server sorting on the client. We know that the users can use any of the servers to stream content or carry out P2P file sharing, but it becomes way easier do such activities if there are dedicated servers on the client.
For instance, a user cannot do P2P file sharing on the US and France servers because of the pressure from the media agencies. Similarly, there are some low bandwidth servers on which sharing large files may lead to inefficient service for other users.
The VPN provider could have made a separate list of servers which does not contain the servers mentioned above, and the users would have got a P2P server list.
A similar case can also me made for streaming servers, but we think we have delivered the idea. Dedicated servers and lists not only help the users in navigating through the server list but also helps the VPN provider to keep the services running smoothly.
Privacy Policy
We already mentioned that this is a Swiss product. We also discussed that Switzerland has some strict privacy laws, which makes it easier for companies to safeguard the privacy of the users.
With such favorable conditions already in place, we expected nothing less that perfection from Perfect Privacy in the privacy department. And to our delight, they delivered perfection only.
Many VPN services boast of a no-logs policy, but they store user’s personal information in one form or the other. It was not the case with Perfect Privacy. They have a 100% no logs policy.
They don’t store any information about the user’s activities inside the VPN tunnel. Along with that, they don’t save the time stamps and IP addresses. They don’t even keep a log of the IP addresses of the VPN servers with which the user got connected.
The data volume flow is monitored for the individual servers, which includes the collective data of all the users connected to that server, and it is not possible to identify an individual from this data.
Generally, the VPN services store the email addresses of the individuals, but Perfect Privacy explicitly mentioned that the users take the help of throw away email addresses to get the first mail which contains the username and the password.
They seem to have no interest in storing the email id of the users, and this kind of thinking aligns with ours.
For the correspondences with the support team, the user can again use throw away emails, and they also encrypt all the correspondence data to maintain secrecy.
There are cookies involved when one visits their website, and they suggest the users visit the official website with a VPN cover to avoid cookies.
They also have a warrant canary which adds to the already strong privacy measures. Warrant canary is a method used by a lot of service providers to inform the users about any kind of non-disclosable government summons.
After a thorough analysis, we think it is safe to say that Perfect Privacy is a safe and transparent service which takes suitable measures to ensure that user’s privacy is not compromised.
Connection Time Analysis
| Trial No. | Time to establish a connection (seconds) |
|---|---|
| 1 | 26.7 |
| 2 | 19.16 |
| 3 | 20.64 |
| 4 | 18.39 |
| 5 | 17.94 |
| 6 | 18.6 |
| 7 | 18.19 |
| 8 | 26.52 |
| 9 | 30.91 |
| 10 | 36.43 |
| Avg. Time In Seconds | 23.348 |
The connection time analysis data provided in the table is for the OpenVPN protocol. We chose the OpenVPN protocol because it is supposedly the slower one among the two protocols available on the service.
The other protocol available is IPSec.
The client takes a lot of time to connect to the internet. An average time of 23 seconds is nowhere near the connection times of the popular VPN products.
The users these days want a product to be as swift as possible, and because the rest of the VPN services are providing a lot lower connection times, Perfect Privacy needs to up their game.
This is one of the very few shortcomings of this service, and if they can find a way to address this issue, then it will not be easy to beat this product.
Speed Test
Speed matters a lot in the VPN service. All the prominent VPN services are relevant only because they continuously provide high speeds with the VPN cover.
Users want to make the most of their high-speed internet connection, and therefore, the faster VPN service is always preferred.
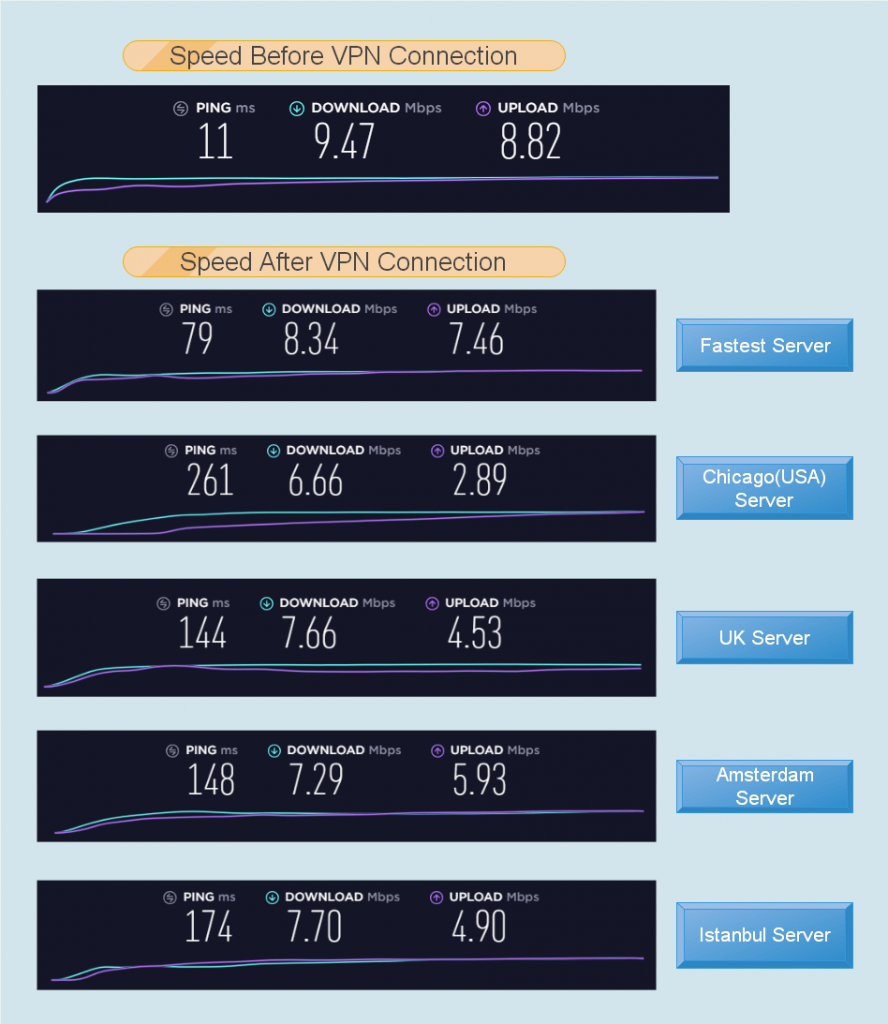
Perfect Privacy does not comes with an automatic server selection or a smart-connect option. So, we manually connected to the geographically closest server for our location.
Boy oh boy! we got some fast speeds on the closest server. The speed after the connection was 97.7% of the original speed. This is among the fastest speeds we have ever experienced.
The situation was a lot similar to the Swiss servers. It was slightly lower than the previous servers, but we were still getting around 97% of the original speeds.
However, things got a lot slower when we connected to the US and the UK servers. We got 76% and 66% of the initial speeds for the two respective server locations.
We had a thirty percent variation of the speeds for the servers across different locations, and a decision to make, thar is if the client is fast or not.
In the past, whenever we have come across a fast VPN service, it was able to give more than 80% of the original speeds for most of the servers in the network.
Perfect Privacy, on the other hand, gave some stunningly high speeds on a few servers and then mediocre on the rest.
We can’t conclusively say that it is a high-speed VPN service. Even though we got some impressive speeds on a few servers, the speeds on the rest of the servers also need to be taken into consideration.
Because of significant differences in the speeds on various servers, we won’t rank Perfect Privacy among the fastest VPN services, but it is also worth mentioning that even the slower speeds were also above the satisfactory level.
The bandwidth available for different server location varies. However, the user can see the available bandwidths on the client itself.
They don’t cap the bandwidth usage for individual users in any way, and similarly, there are no restrictions on speeds as well.
Security
We already know that there are ample advanced security features on the product which we have already discussed at the beginning of the review.
Before going through them again in brief, let us discuss the necessary security features such as protocols and encryptions.
The service comes with the highest encryption level of 256-bit which is the best encryption available. The service also provides the option to scale down the encryption level if the user does not want to lose much of the system ability because of the high-level encryption.
For protocols, the client comes with the OpenVPN and IPSec protocols. The service also supports PPTP protocol, but they don’t provide it in the client because of the low security level.
For proxy servers, they use Squid and SOCKS5 proxies. Both these proxies are enough to suffice the needs of a lot of the users.
The only issue that we can raise at the moment is the number of the protocols available, but rest of the bases have been covered for sure.
The service comes with IPv6 as well as DNS leak protection. Most of the servers have IPv6 support, and only four server locations don’t support IPv6 at the time of the review.
The internet kill switch on the client is also advanced in the sense that it has three different levels. We have already discussed the kill-switch in detail in the above section. The DNS leak settings are also similar to that of the kill-switch.
Apart from these regular security features, the client has loads of advanced security features as well.
Under the cascading feature, the user can connect to a maximum of 4 VPN servers to have a multilayer VPN protection.
NeuroRouting is an exclusive feature of Perfect Privacy which uses artificial intelligence and machine learning to make sure that user’s internet traffic data remains within the VPN network for the most part before reaching the destination.
TrackStop is an ad-blocker which comes along with the service. It has a lot of customizable features along with the conventional ad-blocking service.
The security on the product has turned the VPN network into an impenetrable fortress. We rarely see so many exclusive features in a single product, and the service has not left much for the user to yearn for.
User Interface and Experience
The user interface on the service looks very dull, but at the same time, we don’t think that we have come across any user interface with so many customization options.
So, without wasting any words, let us start from the first tab in the settings window.
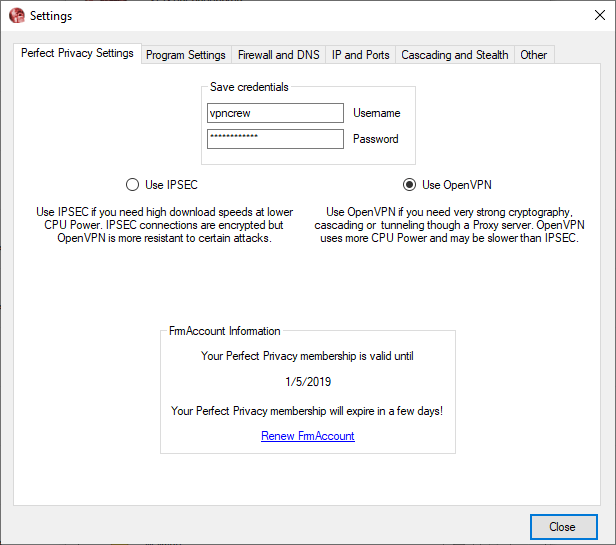
The first tab is ‘Perfect Privacy settings’. The user can choose the protocol and enter the login credentials in this window. The account information is also displayed in this tab.
Next is the ‘Program Settings’ tab. You can change the encryption and modify the server list according to various categories from this tab. Then there are the customizations options as well such as ‘Start with Windows’ and ‘Start minimized’.
It is followed by ‘Firewall and DNS’ tab. The tab contains various settings for kill-switch and DNS leak protection. The settings for both the features is pretty much the same.
IPv6 leak protection is also included in this tab.
Now comes the ‘IP and Ports’ tab. This contains various customization options for port-forwarding. Port-forwarding is one of the advanced features in the VPN service, and it is helpful in certain situations such as gaming.
The penultimate tab in the settings menu is ‘Cascading and Stealth’. And no points for guessing that it contains settings for multi-hopping and Stealth VPN. All the proxy customization options are provided in this window.
The final tab is ‘Other’. It contains information about updates and debugging. The user can also reset the network from this tab.
The client has a lot of customization options and is very functional. But we would also like a bit more flare in the way the client looks. Addition of a few colors won’t hurt anyone, but it will ensure that the client does not seems so dull.
Platforms and Devices

The service is available across all the major platforms which include Windows, MacOS, Android, iOS, Linux, and Routers.
There are no extensions for browsers and no other platform support. When it comes to routers, they have provided the list of routers which are compatible with the service.
The users need to use WiFi routers if they want the VPN cover on rest of their devices as well.
The platform support is very limited in the service, and they need to work a lot on the user accessibility front. With so many platforms and devices being introduced regularly, the VPN services also need to stay on their toes to keep up with the increasing diversity.
Customer Support
Customer support acts as a link between the customer and the service. Many times it is ignored by the services, and they pay the price for it in the long run when the customer queries are not appropriately addressed.
There is no live chat support present on the service. But they have tried to make up for that with a detailed an exhaustive website which goes through all the relevant topics about the product.
The users can find answers to almost all their question by navigating through the website. But, not all them are so patient, and it is too much of a task for them to go through the various sections of the website.
The query ticket system is available, but it is not the swiftest one out there. There is no guarantee that the user will get a response within a few hours.
They need to strengthen the one on one support system for the service, be it with the addition of live chat support or by making sure that the query tickets are addresses within a fixed time frame.
The current state of customer support is not satisfactory at all, and the provider needs to make sure that all the customer issues are addressed quickly and efficiently.
Conclusion
There is no doubt that this product is jam packed with features.
They not only included new and advanced technology with some of the features but also revamped a lot of the conventional features and presented an improved version of those features to the users.
We had no issues with the integrity of the service as well. They were very thorough with the privacy policy, and we deem them as a transparent VPN service.
The speeds varied a lot across the servers, and we were not able to put the finger on the general speed output of the service. It might change a lot from user to user and location to location.
We don’t have issues with the security features at all, and at some points, we felt that they are more than enough. But when it comes to online security, one cannot be sure enough, and therefore all the added features are welcomed.
They have a lot of ground to cover for customer support. If a user comes across some major issue, then he/she might have to wait for long hours to get a proper solution to the problem.
By fixing these minor issues, Perfect Privacy can qualify as one of the big players of the VPN world. But they need to show the same level of commitment which they showed for the features.
